A revolution in compliance tools for operational risk management based on ISO/IEC 27001
A revolution in compliance tools for operational risk management based on ISO/IEC 27001
Stiki Information Security announces a new state-of–the-art risk management tool for risk assessment according to ISO/IEC 27001. The tool provides a comprehensive solution for allowing businesses of all sizes to cost-effectively deploy an effective risk assessment and management along with GAP analysis. Introducing a new user interface with a Office 2007© look and feel, powerful search capabilities and greatly effective handling of assets, RM Studio aims to provide a intuitive and satisfying user experience.
RM Studio is a fully Microsoft compateble risk management tool for ISO/IEC 27001 compliance. It reduces the need for expensive consultants, minimizing senior staff input and eliminates time wasted on inappropriate and cumbersome RA tools. It also reduces the vast amount of time needed to meet the demands of ISO/IEC 27001:2005 accreditation. The software provides a powerful reporting tool with regularly updated ISO/IEC 27002(ISO/IEC 17799) standards and follows the methodology of ISO/IEC 27001:2005. The software has a comprehensive gap analysis module, risk treatment module and risk assessemnt module along with a set of management reports.
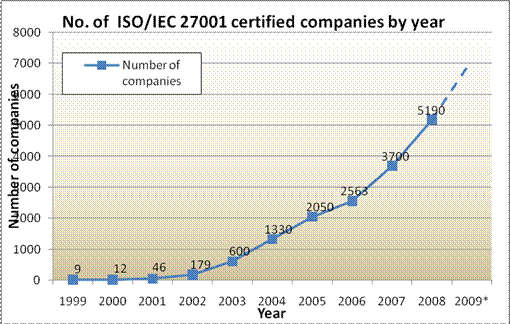
• ISO/IEC 27001 certifications increase every year
• The number of companies certified to ISO/IEC 27001 (formerly BS 7799) is increasing every year and ISO/IEC 27001 is the only auditable international standard which defines the requirements to ensure that sufficient security controls are instituted within the certified organization. Maintaining the ISO/IEC 27001 Certification requires an annual review and three year re-certification in the continual scrutiny.
The shock-free operation of information systems includes measures designed to manage operational risk, prevent conflicts of interest and secure transparency in the market. Additionally, this includes measures to maintain the security of information; i.e. by ensuring authorized access when needed and that the information provided is correct and has not been tampered with.
Further details are available at www.riskmanagementstudio.co.uk